43 which of the following statements about the use of antivirus software is correct
PDF Sample Question Paper 1 Class X Artificial Intelligence ... (iii) Statement 1 is correct but Statement 2 is incorrect. (iv) Statement 1 is incorrect but Statement 2 is correct. 5. Given below are the steps to make a copy of folder 'D:\Myfolder' in 'C:\Documents'. Rearrange the steps in the correct order. (1) (i) Right click anywhere in the folder and select Paste option from the shortcut menu or ... 13.3.9 Flashcards - Quizlet Which of the following statements about the use of anti-virus software is correct? Anti-virus software should be configured to download updated virus definition files as soon as they become available. An attacker sets up 100 drone computers that flood a DNS server with invalid requests. This is an example of which kind of attack? DDoS
13.3.9 - Practice Questions Flashcards - Quizlet Which of the following statements about the use of anti-virus software is correct? - If you install anti-virus software, you no longer need a firewall on your network. - Anti-virus software should be configured to download updated virus definition files as soon as they become available.

Which of the following statements about the use of antivirus software is correct
Which of the following are recommended ... - Brainly.com Which of the following are recommended techniques for protecting computer files and data? Check all of the boxes that apply. A. Back up the system. B. Install firewall software. C. Use the file manager. D. Install antivirus software. E. Update the operating system. F. Use shared folders. G. Use spam protection. Which of the following statements regarding Sigcheck is ... 1. Which of the following statements regarding Sigcheck is correct? (Choose all that apply.) a. Sigcheck examines hidden files. b. Sigcheck examines only executable files. c. Sigcheck can be used to verify that a digital signature is authentic. d. Sigcheck can check for certificate revocation. Cyber Security & Penetration Testing Multiple Choice ... 41. In computer security, which of the following means that computer system assets can be modified only by authorized parties? a. Confidentiality b. Integrity c. Availability d. Authenticity. 42. Which of the following are mainly unskilled and novice hackers who use tools and scripts developed by others to hack into systems? a. White hat hackers b.
Which of the following statements about the use of antivirus software is correct. Which Of The Following Statements About The Use Of Anti ... 1. Which of the following statements about the use of anti-virus software is correct? Anti-virus software should be configured to download updated virus definition files as soon as they become available. Only files that have changed since the last full or incremental backup Add a separate A/C unit to the server room. Termination, Background Checks ️Which of the following statements is true when marketing ... We also use third-party cookies that help us analyze and understand how you use this website. These cookies will be stored in your browser only with your consent. You also have the option to opt-out of these cookies. Solved Which of the following statements are NOT true ... Choose all that apply. a Anti-virus software is used to detect malware. Therefore, anti-virus software is free of all malware. b Malware can only spread through the Internet. c Malware has been found in boot sectors of some operating systems Expert Answer 100% (1 rating) Correct Answer: a. Anti-virus software is used to detect malware. Microsoft digital literacy exam answers - Scrupulous Scribe Which of the following settings can he use to set Windows to periodically check for the latest updates? Internet Options; Windows Firewall; Automatic Updates (Correct Answer) Antivirus Updates Lesson 5: Computer ethics . Michael is creating his own website. While browsing the Internet, he finds some images that he wants to use on his site.
Cyber Security MCQ (Multiple Choice Questions) - javatpoint Explanation: Antivirus is a kind of software program that helps to detect and remove viruses form the user's computer and provides a safe environment for users to work on. There are several kinds of antivirus software are available in the market, such as Kaspersky, Mcafee, Quick Heal, Norton etc., so the correct answer is D. MCQ - Network Security - My Computer Notes Each question is multiple choice type with a single answer. The section consists of 20 questions with multiple-choice options. MCQ - Network Security - Section 1 1: Which of the following is correct in connection with the password policy? Usually, password length must be more than 8 characters CEH Assessment from CEH Flashcards by hadona Diep - Brainscape Firewalls are categorized into two; namely hardware firewall and software firewall. Identify the correct statement for a software firewall. Software firewall is placed between the desktop and the software components of the operating system Software firewall is placed between the router and the networking components of the operating system Which of the following statement is most accurate? A. A ... Which of the following statement is most accurate? A. A reference variable is an object. B. A reference variable refers to an object. C. An object may contain other objects. D. An object may not contain the references of other objects
AZ-500 Exam - Free Actual Q&As, Page 9 - ExamTopics You have an Azure subscription named Subscription1 that contains the resources shown in the following table. You create an Azure role by using the following JSON file. You assign Role1 to User1 for RG1. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Uninstall tamper-protected Sophos Antivirus with ... 22/06/2016 · Following the message, we want to be nice and open the Sophos Endpoint AV Console for the user. Use the call operator (&) to open the .exe. & 'C:\Program Files (x86)\Sophos\Sophos Anti-Virus\SAVmain.exe' With the help of Venkat Sri’s post here on 4sysops, we have the user confirm that the tamper protection has been disabled with a Yes/No ... MTA Security Fundamentals Practice Test 1 Quiz - Quizizz For each of the following statements, select Yes if the statement is true. Otherwise, select ... Install anti-virus software. Enable spam filtering. Turn on Windows Firewall. Tags: Question 12 . SURVEY . ... Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the underlined text ... Which of following statements about IDS are correct ... Which of following statements about IDS are correct? (multiple answer) A. The IDS dynamically collects a large volume of key information and analyzes and identifies the status of the entire system. B. The IDS can block detected policy breaches and attacks. C. The IDS system is comprised of all software and hardware systems for intrusion ...
Question 110 1 point Identify the correct statement for a ... Question 110 ( 1 point ) Identify the correct statement for a software firewall . Question 111 ( 1 point ) Which of the following is an antenna used in wireless base stations and provides a 360 degree horizontal radiation pattern ? Question 113 ( 1 point ) According to the text , which of the following will protect by limiting the ability to ...
MIS chapter 8 - Subjecto.com - Subjecto.com — free essay ... 4) Which of the following statements about wireless security is not true? A) SSIDs are broadcast multiple times and can be picked up fairly easily by sniffer programs. B) Radio frequency bands are easy to scan. C) An intruder who has associated with an access point by using the correct SSID is capable of accessing other resources on the network.
Web Ethics & Safety | Digital Literacy Quiz - Quizizz Which of the following statements defines cyberbullying? Web Ethics & Safety DRAFT. 9th - 12th grade. ... Which of the following is the correct reaction when someone you do not know asks you to add him or her as a friend on Facebook? ... installing anti-virus software. conducting defragmentation. updating anti-virus software. scanning your ...
Security awareness quiz - answers - John Opdenakker A: The correct answer is 2. Passwords should be long enough, minimum 12 or 14 characters is recommended. Passwords should also be random because attackers will have giant lists of predictable passwords they can use to crack passwords or gain access to your online accounts. They should also be unique.
The Antivirus Hacker's Handbook - Page xix - Google Books Result Joxean Koret, Elias Bachaalany · 2015 · ComputersThis book is for you if any of the following statements are true: □ You want to learn more about the security of antivirus products.
Utility Software - ProProfs Quiz Antivirus, trojan, anti-spyware software 5. Which of the following statements is/are correct? A. A virus copies itself automatically between and within computers by attaching itself to another file. B. A worm spreads very fast over a network and often slows down a system. C. Trojans are not viruses because they do not copy themselves automatically
Wiley CPA Exam Review 2008: Business Environment and Concepts O. Ray Whittington, Patrick R. Delaney · 2007 · Business & EconomicsWhich of the following statements is correct regarding the declaration of a stock ... Elimination of the need to continuously update antivirus software. b.
Chapter 7 Flashcards | Chegg.com Most antivirus software is effective against: only those viruses already known when the software is written. In 2004, ICQ users were enticed by a sales message from a supposed anti-virus vendor. On the vendor's site, a small program called Mitglieder was downloaded to the user's machine.

Norton 360 Deluxe 2022 | 5 devices | Antivirus | Unlimited Secure VPN | 1 year | Password Manager | PC/Mac/Android/iOS | Activation code via email
[MCQ's] Infrastructure Security - Last Moment Tuitions Explanation: Spyware is professional malicious spying software that is hard to detect by anti-malware or anti-virus programs because they are programmed in such a skillful way. These types of software keep on collecting personal information, surfing habits, surfing history as well as credit card details. 14. Stuxnet is a _________ a) Worm b) Virus
13.3.9 Practice Questions - Subjecto.com Which of the following statements about the use of anti-virus software is correct? anti-virus software installed on them. If you install anti-virus software, you no longer need a firewall on your network. soon as they become available. Once installed, anti-virus software needs to be updated on a monthly basis.
3.1 Uses of common applications | Software | Siyavula Say if the following statements are TRUE or FALSE. Correct the underlined word(s) if they are false. a. Software updates include improvements to program performance, stability and improved access. b. Software developers use write-only files by selling their software on CDs/DVDs.
CompTIA Security+ Exam Cram: Domain 3.0: Threats and ... Which of the following types of logging events are most commonly found in antivirus software? (Select all correct answers.) A. Updates; B. Dropped packets; C ... Which of the following is a software utility that is used to conduct network assessments over a range of IP addresses and compiles a listing of all systems, devices, and hardware ...
Microsoft Security Bulletin MS13-002 - Critical ... 08/01/2013 · The following software have been tested to determine which versions or editions are affected. Other versions or editions are either past their support life cycle or are not affected. To determine the support life cycle for your software version or edition, see Microsoft Support Lifecycle. Affected Software Operating System Component Maximum Security Impact …
Cyber Security & Penetration Testing Multiple Choice ... 41. In computer security, which of the following means that computer system assets can be modified only by authorized parties? a. Confidentiality b. Integrity c. Availability d. Authenticity. 42. Which of the following are mainly unskilled and novice hackers who use tools and scripts developed by others to hack into systems? a. White hat hackers b.
Which of the following statements regarding Sigcheck is ... 1. Which of the following statements regarding Sigcheck is correct? (Choose all that apply.) a. Sigcheck examines hidden files. b. Sigcheck examines only executable files. c. Sigcheck can be used to verify that a digital signature is authentic. d. Sigcheck can check for certificate revocation.
Which of the following are recommended ... - Brainly.com Which of the following are recommended techniques for protecting computer files and data? Check all of the boxes that apply. A. Back up the system. B. Install firewall software. C. Use the file manager. D. Install antivirus software. E. Update the operating system. F. Use shared folders. G. Use spam protection.

















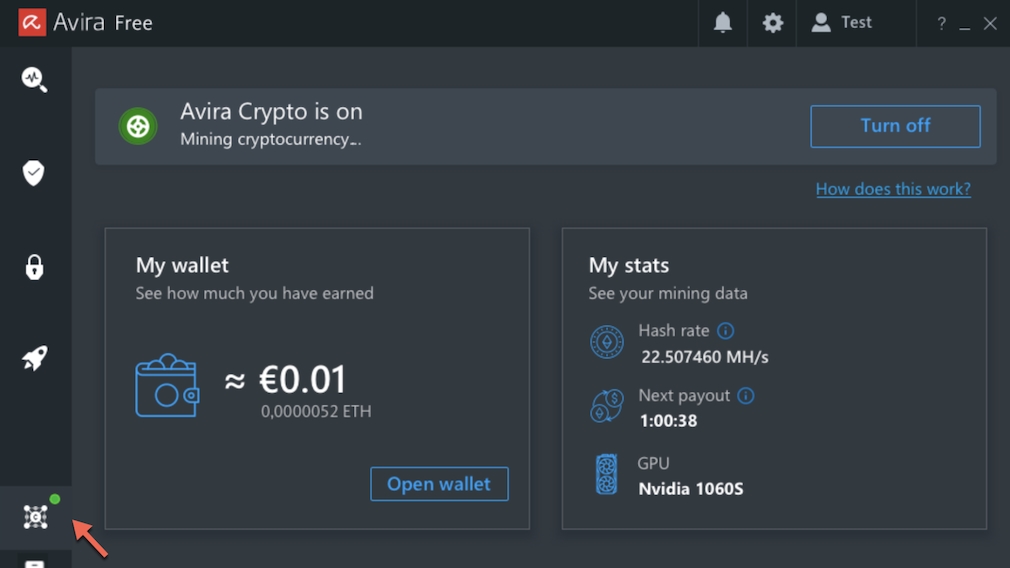




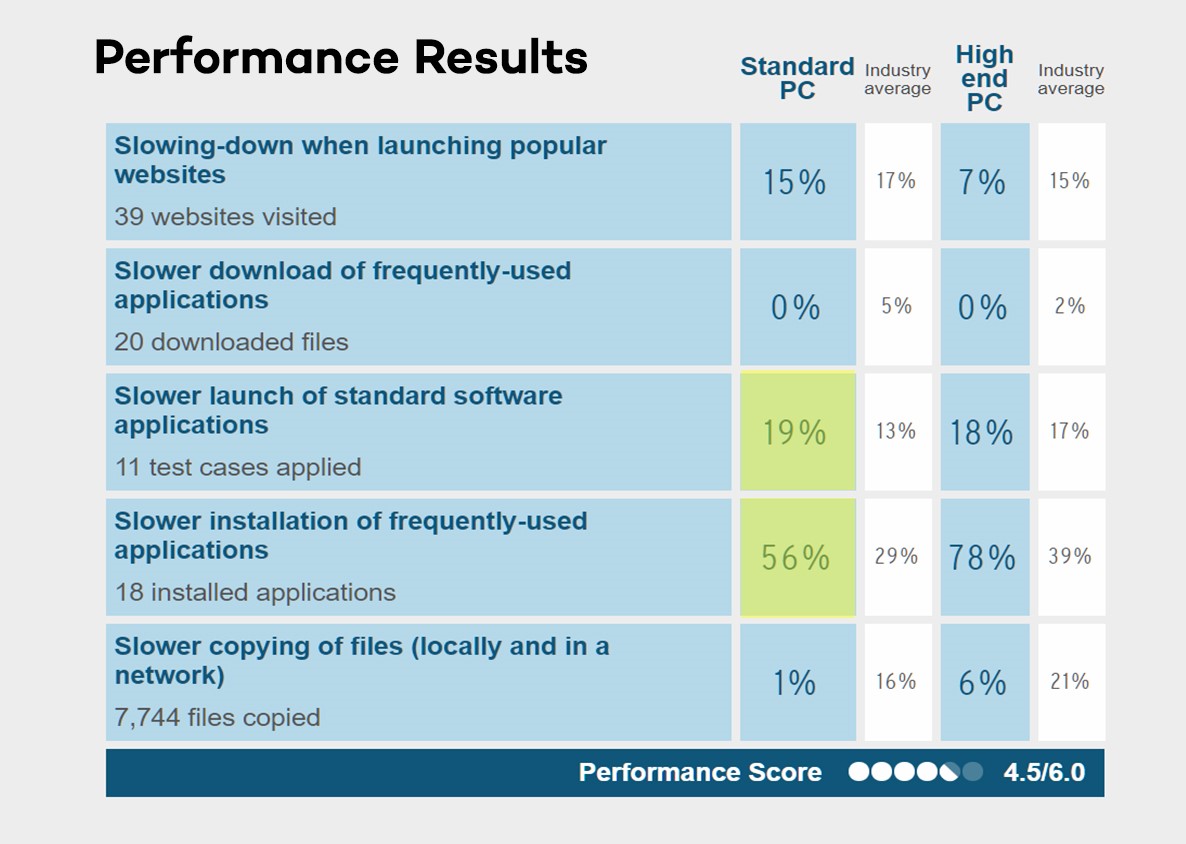









0 Response to "43 which of the following statements about the use of antivirus software is correct"
Post a Comment